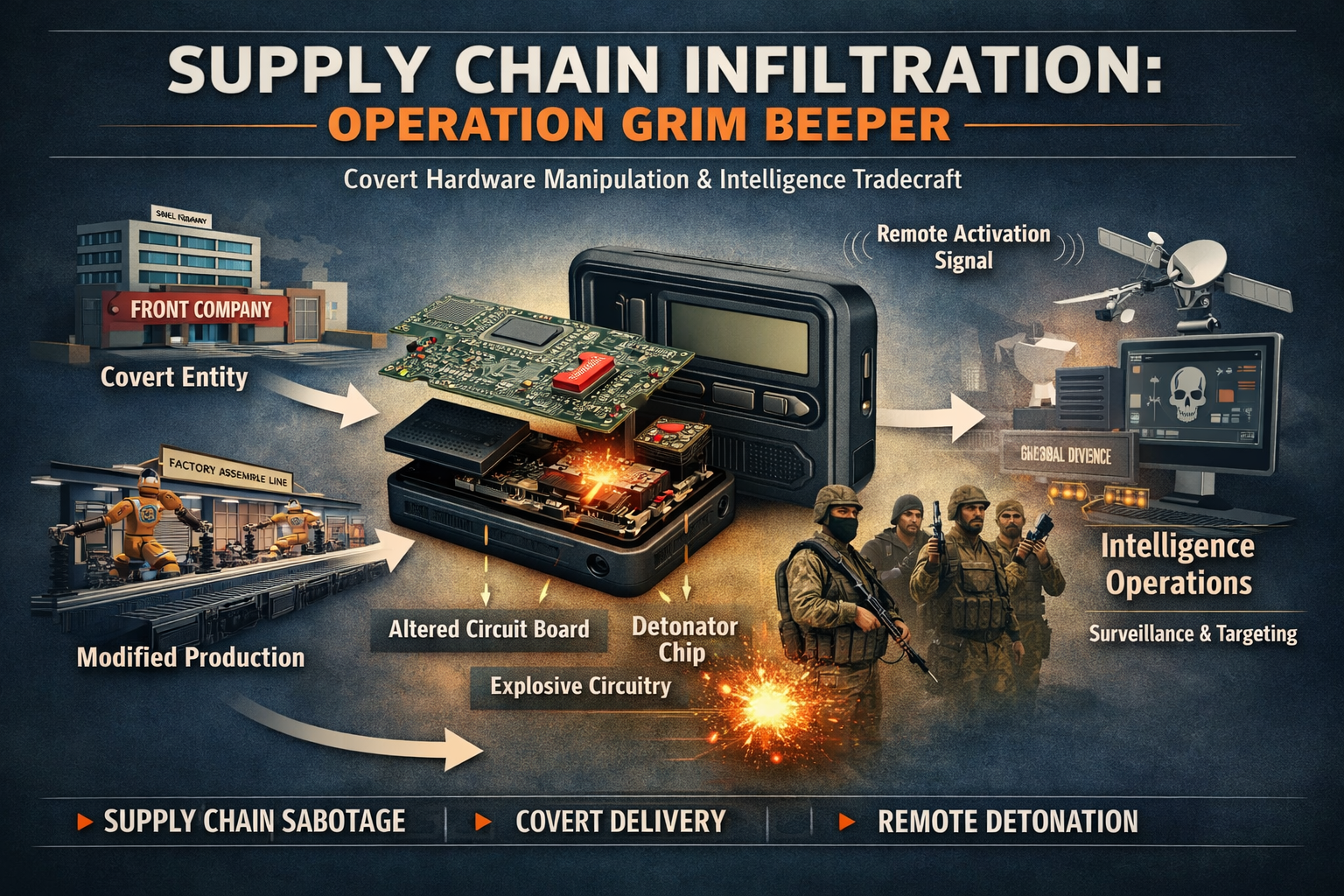
Operation Grim Beeper and the Weaponization of Procurement Networks
The September 2024 pager detonations in Lebanon represent a case study in long-duration intelligence tradecraft applied to industrial and digital systems. Reporting from Reuters, a documentary source, policy commentary, and regional cyber analysis collectively describe an operation that fused counterintelligence, corporate deception, cyber penetration, and distributed kinetic action.
The event was not a single strike but a layered campaign designed to degrade Hezbollah’s operational ecosystem.
The core mechanism was not the explosive payload itself but the manipulation of Hezbollah’s security logic. Hezbollah shifted from smartphones to pagers to reduce exposure to Israeli digital surveillance. That decision created a procurement vulnerability. Israeli intelligence reportedly exploited that vulnerability by inserting modified devices into Hezbollah’s supply chain, allowing devices to circulate undetected for months before synchronized activation.
From a tradecraft perspective, the operation integrated multiple intelligence disciplines: supply-chain mapping, covert manufacturing, clandestine distribution, cyber-enabled targeting, and coordinated activation. Each layer required independent operational security. Failure at any stage would have compromised the broader campaign.
Operational Architecture and Tradecraft
Reuters reporting indicates Hezbollah ordered approximately 5,000 pagers from a Taiwanese manufacturer and that Israeli intelligence inserted modified circuit boards containing explosives at the production level. Sources cited by Reuters described up to three grams of explosive per device, activated by coded messages. The devices circulated for months without detection, indicating either advanced concealment techniques or limitations in Hezbollah’s inspection protocols.
The documentary source expands on this architecture, describing a longer preparatory timeline and early-stage surveillance devices that predated the pager operation. While Reuters does not confirm the full decade-long timeline, it corroborates that the plot was months in the making and constituted a major counterintelligence breach.
Policy commentary characterizes the operation as a composite of four sub-operations: mapping procurement pathways, engineering miniaturized explosives, embedding production access, and coordinated activation. This modular approach aligns with the intelligence doctrine that compartmentalizes risk and preserves deniability.
Device Selection: Why AR-924–Class Pagers Were Operationally Attractive
The pagers cited in Reuters reporting were Apollo AR-924–class alphanumeric pagers, a legacy one-way communication device category that Hezbollah adopted as a counter-surveillance measure. From an intelligence tradecraft perspective, these devices offered several attributes that made them attractive for clandestine use and, at the same time, ideal for supply-chain sabotage.
Long Battery Life and Operational Persistence
AR-924–class pagers are designed to operate for extended periods without recharging. This reduces the need for frequent power cycling, physical handling, or replacement, lowering observable logistics signatures and exposure to technical surveillance.One-Way Communications Architecture
These pagers receive messages but do not transmit data. This eliminates return-channel telemetry that could be exploited for geolocation or network mapping, making them attractive to organizations attempting to evade signals intelligence tracking.Minimal Firmware and Software Attack Surface
Legacy pagers typically run simple firmware with limited processing capability, no internet connectivity, and no modern operating system. This reduces susceptibility to conventional cyber exploitation techniques such as remote malware injection or over-the-air firmware manipulation.Lack of Integrated Sensors and Telemetry
Unlike smartphones, pagers lack GPS, accelerometers, microphones, cameras, and radios designed for bidirectional data. This limits passive data leakage and reduces the digital footprint available to adversary intelligence services.Perceived Security Through Obsolescence
Hezbollah’s shift toward pagers reflects a broader security assumption: older technology is less vulnerable to modern surveillance. This assumption proved flawed when adversary capabilities targeted the physical supply chain rather than digital networks.
Ironically, these same attributes made the devices ideal for covert hardware manipulation. The absence of sophisticated firmware monitoring, secure boot mechanisms, or hardware attestation allowed modified circuit boards and explosive components to be integrated during manufacturing without triggering detection. The reliance on external procurement further shifted the security boundary from encrypted networks to global manufacturing and logistics systems.
The operational mechanics of Operation Grim Beeper are not unique to non-state actors or Middle Eastern conflicts. The same procurement structures, licensing frameworks, and distributed manufacturing models underpin U.S. defense procurement, telecommunications infrastructure, industrial control systems, and consumer IoT markets. The operation therefore functions as a proof-of-concept for hardware-based covert action against modern supply chains, with implications extending beyond Hezbollah to any organization reliant on globally sourced electronics.
Hardware Supply-Chain Threat Model: Structural Vulnerabilities Exposed
Operation Grim Beeper illustrates a class of vulnerabilities that extend beyond non-state actors and into national critical infrastructure, defense procurement, and commercial technology ecosystems. The operation targeted the manufacturing and procurement layer rather than digital networks, demonstrating a tradecraft vector that bypasses conventional cybersecurity controls.
1) Manufacturing as an Intelligence Surface
Modern hardware production is globally distributed across contract manufacturers, licensing partners, and third-party assemblers. Each intermediary represents a potential covert access point. Adversaries can introduce modified components, covert circuitry, or firmware changes during assembly without requiring post-delivery access.
2) Brand Licensing and Third-Party Production Risk
Licensing agreements allow third parties to manufacture devices under established brand names. This practice creates a structural gap between brand identity and production control. End users often assume branded hardware originates from a trusted source, while actual manufacturing occurs in opaque subcontracting environments.
3) Procurement as Targeting Mechanism
Organizations often distribute devices based on role, function, or hierarchy. This logistical process can become an implicit targeting system if hardware is compromised. In the Hezbollah case, internal distribution determined who carried modified devices, effectively outsourcing target selection to the organization itself.
4) Legacy Technology Blind Spots
Legacy systems are often assumed to be secure because they lack modern connectivity. However, their simplicity also means fewer integrity checks, no hardware attestation, and limited forensic capability. Physical modification of legacy hardware can be difficult to detect without destructive testing.
5) Corporate Front Entities and Industrial Cover
Shell companies embedded in legitimate supply chains provide plausible commercial cover for covert manufacturing. Intelligence services can leverage corporate structures, financial transactions, and licensing frameworks to create long-term covert production infrastructure with minimal suspicion.
6) Downstream National Security Implications
The same tradecraft model applies to defense electronics, telecommunications equipment, medical devices, and industrial control systems. Compromised hardware could enable espionage, sabotage, or kinetic effects without traditional cyber intrusion.
7) Detection and Mitigation Constraints
Hardware assurance requires destructive testing, supply-chain provenance verification, and component-level inspection. These measures are expensive and rarely applied at scale in commercial procurement. As a result, supply-chain sabotage can persist undetected for extended periods.
Shell Companies and Industrial Cover Infrastructure
A central tradecraft element described in the documentary source is the use of shell companies to embed Israeli-controlled manufacturing inside Hezbollah’s procurement pipeline. The primary entity cited is BAC Consulting, registered in Budapest and operating under a licensing agreement with Taiwanese pager manufacturer Gold Apollo. Under this arrangement, BAC Consulting was authorized to manufacture and sell devices under Gold Apollo’s brand name.
This structure exploited standard electronics industry practices. Licensing agreements and outsourced manufacturing are routine, allowing third-party producers to build devices under established brand identities. This provided a commercially plausible explanation for why Gold Apollo-branded pagers were not manufactured in Taiwan.
According to the documentary, BAC Consulting maintained corporate registration, a listed office address, and a public-facing executive identity, creating a veneer of legitimacy sufficient to pass supplier vetting. The source further claims that BAC Consulting functioned as a Mossad-controlled front company, with additional shell entities used to obscure attribution. Reuters does not independently confirm these corporate details but notes that devices were modified at the production level and that attribution was initially opaque.
Operationally, the shell company structure served multiple intelligence functions:
Manufacturing Control: Integration of modified boards and explosive material during assembly rather than post-import tampering.
Attribution Buffer: Corporate layering created plausible deniability and delayed forensic attribution.
Procurement Insertion: Hezbollah procurement officers believed they were sourcing legitimate branded equipment through conventional commercial channels.
Distribution Shaping: Pricing and procurement tactics reportedly discouraged non-Hezbollah buyers while incentivizing bulk purchases by Hezbollah intermediaries, allowing selective distribution control.
From a tradecraft perspective, this represents industrial-scale covert infrastructure. Instead of inserting devices at the user level, the operation reconfigured the production environment itself. The shell company functioned as an intelligence asset embedded in the global manufacturing ecosystem.
Historically, intelligence services have used front firms for finance, logistics, and cover employment. In this case, the front firm reportedly functioned as a covert weapons production node operating within legitimate global supply chains.
Cyber Penetration, AI Targeting, and Multi-Domain Integration
The Arab Center DC analysis situates Operation Grim Beeper within a broader Israeli cyber and intelligence campaign against Hezbollah. Israeli cyber operations reportedly disrupted communications, enabled espionage, and supported targeted killings of senior leadership. The pager detonations are described as one phase in a multi-domain campaign that included cyber infiltration of communications systems and subsequent assassinations of senior Hezbollah officials.
According to the source, Israeli cyber capabilities, including Unit 8200 and AI-enabled targeting systems, allowed Israel to build detailed target banks, monitor leadership routines, and conduct coordinated strikes. These capabilities reportedly enabled the assassination of multiple senior Hezbollah officers following the pager operation.
From an intelligence tradecraft standpoint, this suggests Operation Grim Beeper was not an isolated technical exploit but part of a layered intelligence campaign combining human intelligence, signals intelligence, cyber surveillance, AI-assisted targeting, and kinetic operations. The pager devices served as both weapons and sensors, degrading morale and forcing Hezbollah to divert resources to communications security.
This integration reflects a modern intelligence model where procurement sabotage, cyber surveillance, and precision targeting operate as a continuous system rather than discrete missions.
Targeting Logic and Organizational Mapping
The detonations functioned as indirect targeting. Hezbollah’s internal distribution of pagers determined who was affected. This approach offloaded targeting decisions onto the adversary’s organizational processes. From an intelligence standpoint, this is a form of self-selection targeting, where adversary logistics become the targeting mechanism.
The effect was dual-use. Injuries removed personnel from operational roles, while distribution patterns implicitly mapped organizational structure. Device allocation reflected rank and function, enabling adversary mapping through forensic analysis and subsequent intelligence exploitation.
Commentary notes that a high ratio of injuries to fatalities imposes greater logistical strain on adversaries. Whether this was a deliberate design objective or an emergent property of small payloads remains unresolved across sources.
Strategic Signaling and Psychological Operations
Beyond physical damage, the operation served as strategic signaling. Penetration of procurement systems demonstrates institutional patience and systemic access. It signals that even legacy technologies are vulnerable to state-level manipulation.
The documentary and sources from Arab Center DC describe widespread distrust of electronic systems among Hezbollah personnel and regional actors. From a national security perspective, this aligns with psychological operations doctrine: undermining confidence in systems can degrade adversary capacity without continuous kinetic engagement.
Legal and Policy Context
The sources diverge sharply in their legal interpretations. The documentary source includes extensive discussion of international humanitarian law principles such as distinction, proportionality, and prohibitions on booby traps disguised as civilian objects, with multiple legal experts arguing potential violations.
Policy commentary frames the operation as lawful and strategically justified against a designated terrorist organization. Reuters does not adjudicate legality; instead, it frames the event as a significant counterintelligence breach with escalation risk.
For intelligence tradecraft analysis, the legal debate informs operational design, deniability structures, and post-operation information campaigns, but does not alter the underlying tradecraft architecture.
The Negative Space
Several unresolved gaps emerge across the combined reporting.
First, shell company attribution remains partially uncorroborated. The documentary provides detailed claims regarding BAC Consulting and additional front entities, while Reuters confirms production-level modification but does not independently verify corporate structures or ownership.
Second, casualty figures and targeting scope diverge across sources. Reuters reports limited fatalities and several thousand injuries. Other sources cite broader leadership decapitation effects and civilian exposure. These discrepancies reflect differing evidentiary standards and narrative objectives.
Third, the operational timeline is inconsistent. Reuters states the operation was months in the making, while the documentary asserts preparatory activity beginning years earlier. The linkage between early surveillance efforts and the pager operation is not fully substantiated across sources.
Fourth, the activation architecture remains opaque. Sources reference coded messages and remote detonation but provide no technical detail on transmission protocols, encryption mechanisms, redundancy controls, or fail-safe measures. These details are central to understanding operational risk and command-and-control resilience.
Fifth, cyber and AI-enabled targeting integration is described at a conceptual level. The Arab Center DC analysis references AI-assisted target banking and Unit 8200 capabilities but does not document data pipelines, validation procedures, or decision thresholds for kinetic action.
Sixth, detection and mitigation mechanisms are underexplored. None of the sources detail Hezbollah’s hardware inspection protocols, supply-chain vetting processes, or counterintelligence auditing frameworks, limiting assessment of why the compromise persisted undetected.
Finally, strategic doctrine remains undisclosed. Reuters frames the event as counterintelligence penetration and escalation signaling, policy commentary frames it as deterrence, and regional analysis frames it as cyber-dominant warfare. No primary-source doctrinal guidance or official strategic rationale is publicly available.
Why This Matters
From a national security and intelligence tradecraft perspective, Operation Grim Beeper demonstrates the maturation of supply-chain infiltration as a covert action vector and its integration with cyber surveillance, AI-enabled targeting, and kinetic operations. It merges industrial production, corporate deception, procurement manipulation, and synchronized activation into a unified operational system.
The episode reframes legacy technology risk. Low-connectivity systems are not inherently secure; they simply shift the attack surface from software to manufacturing and logistics. Procurement networks, licensing agreements, and third-party manufacturing now constitute operational terrain.
The operation also highlights a structural asymmetry. Hardware assurance requires destructive testing, provenance verification, and component-level auditing, measures that are rarely implemented at scale outside classified defense programs. This creates a persistent vulnerability in both commercial and national security systems.
Finally, the case underscores the convergence of intelligence services and industrial ecosystems. Future covert operations may rely less on traditional human asset insertion and more on structural manipulation of production environments, logistics networks, and data systems embedded in global commerce.
Referenced Reporting
Reuters: “Israel planted explosives in Hezbollah’s Taiwan-made pagers, say sources”
Chronicles Of Sleep (YouTube): “How Mossad Built Fake Companies to Sell Explosive Pagers: Operation Grim Beeper”
Hudson Institute: “The Brilliance of ‘Operation Grim Beeper’”
Arab Center Washington DC: “The Impact of Israeli Cyber Operations on Hezbollah”
* All analysis and conclusions are original to Gear Bunker Media.