
Iran Nuclear Talks: Diplomacy or Deception?
As nuclear talks resume in Oman, Iran is facing internal unrest, covert pressure, and growing military risk. The negotiations raise a harder question: can diplomacy work when the regime itself may not survive?

North Korean APT37 Reaper Expands Attack Matrix Beyond Korean Peninsula
Once focused on the Korean Peninsula, North Korea’s APT37 Reaper is now targeting European drone makers and global industries in a widening cyber espionage campaign.

Sketchy Dudes Wear Breitling
“Sketchy dudes wear Breitling” is an observation rooted in real-world use. We look at the origins of the saying, what it actually means, and why its reputation continues to influence how Breitling is perceived and purchased today.

How Do I Optimize My Website for Better Visibility in AI Search?
AI search engines retrieve and summarize knowledge rather than rank pages. This guide explains how to structure content, entities, and technical SEO to increase visibility in ChatGPT, Perplexity, Brave, and Google AI Overviews.
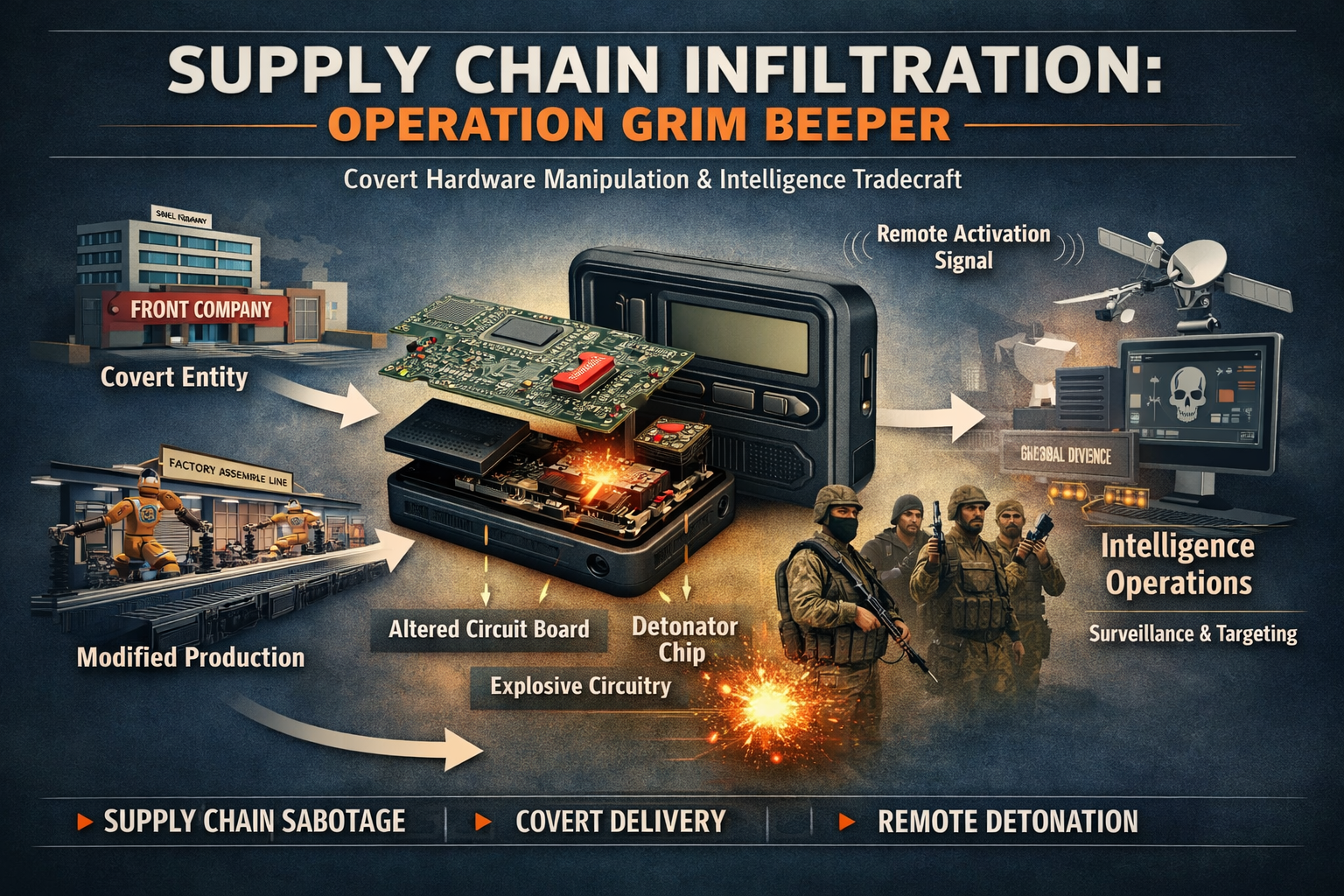
Operation Grim Beeper and the Weaponization of Procurement Networks
An in-depth tradecraft analysis of Operation Grim Beeper and how global supply chains, shell companies, and legacy devices became part of a covert intelligence operation.

The Modern Identity Footprint: Signals, Documents, and Information Exhaust
Identity isn’t stolen in a single moment—it’s built over time. This in-depth Gear Bunker Media analysis breaks down how paper trails, device signals, RFID, SIGINT-style collection, and data exhaust quietly assemble a usable profile—and how real-world controls like shredding standards, Faraday isolation, air-gapping, and compartmentalization actually reduce exposure.

Threema, Signal, and Dust: What Secure Messaging Comparisons Leave Unsaid
Threema, Signal, and Dust are often grouped together as secure messaging apps, but they are built for different use cases. This analysis examines anonymity, metadata, server location, and data control to explain how each platform handles secure communication.

Working in the Negative Space of Content and Analysis
In an era of content saturation, originality often comes from what others overlook. This article explores content gap analysis through the concept of negative space—identifying missing context, weak explanations, and unresolved questions to create meaningful, search-driven value.

Inside the Go-Bag of an Undercover Investigative Journalist
An analysis of the real-world tools and tradecraft used by an undercover investigative journalist, focusing on plausibility, cover scrutiny, and minimizing digital and physical exposure.